
In 2025, being online is no longer optional. Work, banking, communication, learning, and entertainment all depend on internet access. But as digital convenience grows, so does digital risk. Cybersecurity is no longer a technical topic for experts only — it has become a life skill for everyone who uses the internet. Whether you work remotely, run a small business, or simply browse social media, your personal security depends on how careful and informed you are.
Most cyberattacks do not target large corporations. They target individuals. Why? Because individuals are easier to deceive. A company may have an IT department. You do not. Hackers know this. They exploit distraction, lack of knowledge, and emotional reactions. A single click, weak password, or careless login can expose years of personal data.
Cybersecurity is not about fear; it is about awareness. Once you understand the basic mechanisms behind cyber threats, staying safe becomes much easier. Protection does not require extreme tools. It requires consistent habits.
Passwords are still the first line of defense. Even with new technologies, passwords remain the gatekeepers to your online identity. Weak passwords are an invitation to intrusion. Repeating the same passwords multiplies that risk. Every account you own should have its own unique password. Complexity matters. Length matters. Unpredictability matters.
A password manager is not a luxury; it is a safety tool. It generates strong passwords and stores them securely. This eliminates the need to memorize dozens of combinations and prevents password reuse. Security becomes automatic instead of stressful.
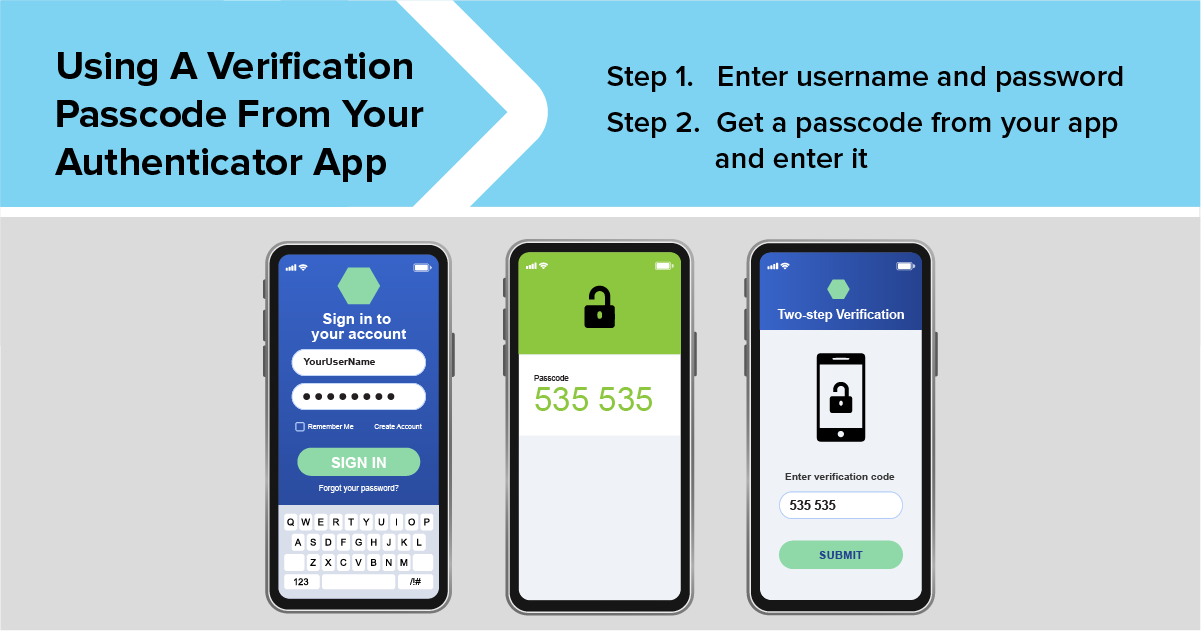
Two-factor authentication adds another barrier between hackers and your accounts. A password alone is no longer enough. With 2FA, a second form of verification is required — a temporary code, authentication app, or biometric confirmation. Even if your password leaks, access remains blocked.
Updates may seem annoying, but ignoring them is dangerous. Software updates often include security fixes for newly discovered vulnerabilities. Running outdated software is like leaving a window open in a bad neighborhood. Cybercriminals search for these weaknesses actively. When you update, you close known entry points.
Phishing remains one of the most common attack methods. Hackers send emails, messages, or fake websites that imitate real companies. They create urgency. They trigger emotion. They pressure decisions. A single email can link to a fake login page designed to steal credentials.
Learn to question unexpected contact. Legitimate companies rarely demand immediate action by email alone. Look closely at sender addresses, spelling, and tone. If something feels off, it probably is.
Your home network is also part of your digital security. Wi-Fi routers often run outdated firmware and default passwords. Many users never change them. This makes exploitation easy. Modern encryption and custom passwords reduce risk significantly. Your internet connection is a digital doorway. Secure it properly.
Backing up data protects you from more than cybercrime. It protects you from hardware failure, software corruption, and human mistakes. When files live in only one place, they are fragile. Cloud storage combined with external backups creates redundancy. Redundancy creates resilience.
Account monitoring is another overlooked habit. Many services offer login activity history and alerts. Enabling notifications for changes gives you early warning. Early response often prevents damage.
VPNs add privacy, especially when working on public networks. While they do not make you invisible, they reduce exposure. They encrypt traffic and protect sensitive information when using cafés, airports, or shared networks.
Education is the strongest defense. Cybersecurity is not a box you check once. It evolves. Hackers adapt. New scams appear constantly. Reading updates, staying curious, and questioning unknown requests are habits of secure users.
Reporting suspicious activity helps protect more than just you. It protects the online ecosystem. When platforms receive reports, they improve detection systems. Silence helps attackers more than victims.
Cybersecurity is not about paranoia. It is about control. When you adopt the right habits, online life becomes safer without becoming complicated. The goal is not perfection — it is awareness.
Many cyber incidents start with human error rather than technical failure. The strongest defense is not software. It is behavior.
Remote workers, freelancers, and entrepreneurs face greater risk because they often manage their own security. One device breach can expose client data, finances, and communications. Security is not optional when work happens online.
Privacy deserves attention too. Data is valuable. Not only to marketers, but also to attackers. Social media oversharing, public profiles, and weak settings expose information that may later become leverage.
Good cybersecurity does not isolate you. It empowers you. You continue using technology with confidence instead of fear.
The internet will not become safer overnight. But your digital world can.
Protection is not about hiding.
It is about staying in control.






